A web application firewall (WAF) is a specific form of application firewall that filters, monitors, and blocks HTTP(S) traffic to and from a web service. By inspecting HTTP traffic, it can prevent attacks exploiting a web application’s known vulnerabilities, such as SQL injection, cross-site scripting (XSS), file inclusion, and improper system configuration.
Just as a virtual or physical appliance, a WAF cloud service prevents vulnerabilities in web applications from being exploited by outside threats.
Description and Use cases
Cloud WAF service combines a cloud-delivered as-a-service deployment with a subscription model.
WAFs use a combination of rule-based logic, parsing, and signatures to detect and prevent attacks. Cloud WAF often comes packaged with load-balancing capabilities, including both local and global, site-failover, high availability and health monitoring.
Challenges
A WAF protects applications against sophisticated Layer 7 attacks that might otherwise lead to loss of sensitive data, systems being hijacked by attackers, and downtime.
Although WAFs won’t “fix” Web app vulnerabilities, it can identify those vulnerabilities and implement security controls over incoming HTTP(S) traffic that might cause a threat to those vulnerable apps.
A WAF has two main uses: visibility into incoming HTTP(S) traffic and the ability to fend off attacks, where a Web application is known to be vulnerable, until the code can be fixed. Also, a WAF also might help satisfy compliance needs.
How can WAF as Service help?
Moving WAF from the premises to the Cloud, and optionally combining it with anti-DDoS services one can benefit from traffic relieved from web site specific attacks passing through the perimeter devices. WAFs are not an ultimate security solution, rather they are meant to be used in conjunction with other network perimeter security solutions such as network firewalls and intrusion prevention systems to provide a holistic defense strategy.
Advantages
Cloud deployment means fast implementation, no changes to the on-premises infrastructure, no CAPEX expenses and (almost) no overhead in administrative tasks.
Deployment
Cloud WAF services perform as reverse proxies by design, and the adoption of more-recent transport layer security (TLS) suites that require in-line traffic interception (man in the middle) to decrypt, have reinforced this type of use.
A reverse proxy is a type of proxy server that retrieves resources on behalf of a client from one or more servers. These resources are then returned to the client, appearing as if they originated from the reverse proxy server itself. Unlike a forward proxy, which is an intermediary for its associated clients to contact any server, a reverse proxy is an intermediary for its associated servers to be contacted by any client.
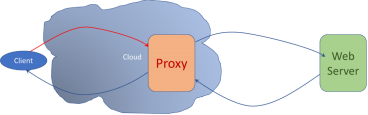
‘Transparent’ refers to the fact that the HTTP traffic is sent straight to the web application, therefore the WAF is transparent between the client and server.





