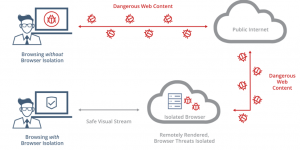
Browser Isolation (also known as Web Isolation) is a technology that contains web browsing activity inside an isolated environment, like a sandbox or virtual machine, in order to protect computers from any malware the user may encounter.
This isolation may occur locally on the computer or remotely on a server.
Browser Isolation technology provides malware protection for day-to-day browsing by eliminating the opportunity for malware to access the end user’s device.
Challenges
While the concept of RBI provides very strong security by disabling any type of browser-based attack on the user, it still faces two major challenges. These are scalability and cost.
How can this technology help you?
Modern RBI systems bring solutions to these challenges in the form of grid distributed architectures (for scalability) and swapping virtualization for containerization (for cost).
The concept of Browser Isolation was the result of thinking through what it would take to completely stop web-based malware from infiltrating a network. Instead of trying to keep users away from unsafe websites, isolated browsing allows users to safely access any website, even if it is malicious. Browser Isolation technology adopts a Zero Trust approach in assuming no web content is safe. All user browsing activity is moved to an isolated environment away from the user’s computer. Since no web content actually ever reaches the user’s computer, malware has no entry point into the system.
Advantages
Protection From Malicious Websites
Because no local code execution happens on the user’s computer, users are protected from all malicious websites.
Protection From Malicious Emails
With Web Isolation, all web-based emails are rendered harmlessly in the remote server, and links in email clients are automatically opened in the remote server as well.
Protection From Malicious Downloads
Administrators can finely control which files users are permitted to download, and all permitted downloads are first scanned to eliminate threats.
Anonymous Browsing
Advanced anonymous browsing capabilities mask users’ true identities.
Data Loss Prevention
Built-in DLP capabilities protect corporate data from being accidentally or intentionally exfiltrated. These capabilities allow an administrator to restrict the files a user can upload to the internet.
User Behavior Analytics
Organizations can obtain analytics into users’ web activities, which can be used for compliance monitoring, and to detect insider threats and unproductive employees.