What is Digital Risk Management?
We can simply define “digital risk” as the consequences of adopting new technologies. These consequences are new and unexpected. Managing digital risk means that you understand the implications of adopting certain technologies—in other words, adopting technologies in a way that lowers digital risk within your organizations.
Digital risk refers to unwanted—and often unexpected—outcomes stemming from digital transformation and the adoption of related technologies.
Lack of visibility - without discovery solutions in place the companies are unable to identify their digital assets (websites, domains etc), APIs (on premise and cloud), data transfers and users activities over messaging platforms or PII data for compliance reasons.
Phishing attacks and impersonation attempts
Phishing attacks and impersonation attempts are increasing year over year and without a proper solution able to detect impersonation a company is prone to ransomware, malware or leaked data incidents.
Most enterprise messaging platforms lack granular control over file transfer, desktop sharing and meeting participants.
Lack malware detection and protection
Most enterprise messaging platforms lack malware detection and protection for attacks with infected files or links.
How can this technology help you?
Increased visibility across your digital assets and cloud environment
Better control over personal data of your end users (customers, partners)
Provides a better context for your data and users in an perimeter-less world
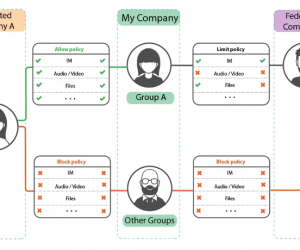
Granular policy for all activities on messaging platforms (e.g. IM or file sharing) controlling external and internal traffic. Define policies for specific team channels, groups or base them on communication participants (external, internal or guest).
Audio and Video analysis on recorded meetings for DLP and discovery needs. Transcript all recorded meetings to audio, Make meeting Searchable using eDiscovery, Inspect meeting audio and video content by DLP policies, Smart DLP incidents with link to video and transcript time.
Real time scanning of all content before it reaches end user devices. Prevent security threats that exploit the human nature factor.
Granular security to automatically restrict access to, restrict sharing of and encrypt content based on the presence of sensitive data including PII, PHI and other confidentiality factors.
Track access to sensitive data, ensuring transparency and accountability. Dynamically add a watermark to Word, PowerPoint, Excel and PDF documents for security and auditing purposes.
Contact us
to find out what DRM solution is right for your needs.