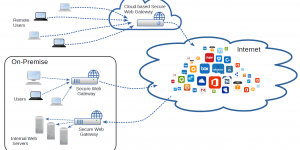
The “Secure Web Gateways” are solutions positioned in the network path between users and internet web servers (“web proxy” systems), which allow enforcing established policies for this type of users activities and preventing external threats which may use this entry path. Their typical actions include monitoring, inspecting and filtering of this type of traffic.
The full spectrum of provided functionalities is usually extended by integration with additional components or solutions such as antivirus scanning engines, sandbox based antimalware systems, data loss prevention components and Cloud Access Security Brokers (CASBs).
By deployment location, the Secure Web Gateways solutions may be classified as on-premises deployments, cloud deployments and hybrid deployments – the deployment has both on-prem and cloud based components, usually with common policies and unified management over them.
By the relationship versus the two entities which pass traffic via the Gateway – the users and the web servers – the “Secure Web Gateway” may work as a “forward proxy” – when it is deployed with the purpose to protect the users by processing the user’s traffic with internet web servers, or as a “reverse proxy” – when it is deployed with the purpose to protect the web servers by processing the web server’s traffic with external users coming over the internet.
Challenges
The potential issues associated with web traffic are numerous, such as the possibility to pass unwanted, mal-intent traffic, potentially carrying malware or viruses, or exfiltrating confidential data, or the loss of productivity induced by users spending time and wasting bandwidth when accessing various entertainment sites during work time.
How can this technology help you?
The IT security functionalities which “Secure Web Gateways” typically provide and are targeted by potential customers are:
Content Inspection
Provides filtering of unwanted URLs, categories, and media types.
SSL/TLS inspection
Enabling visibility into encrypted traffic - which allows preventing hidden threats.
Application Visibility and Control
Allows identification of used cloud based applications. This may expose the so called ``shadow IT`` usage, and allows to control both the access and the functionalities of these apps.
Anti-malware capabilities
Allows to identify and stop known malware before it reaches the IT system. Some solutions may even prevent ``zero-day malware`` activities.
Advantages
One, more specific and recent feature, which underscores the value which a “Secure Web Gateways” may provide, versus other IT security solutions which target the users – internet web servers network traffic, is the capability to decrypt the TLS 1.3 based encrypted traffic, due to their “web proxy” style of operation. That is, of course, if the targeted solution’s vendor has developed the capability into its product.