Cloud Workload Protection Platforms – CWPP – is the protection of the integrity of containers.
This includes everything from the applications they hold to the infrastructure they rely on. Container security needs to be integrated and continuous.
Challenges
A container environment, in general, encompasses images, containers, hosts, container runtime, registries and orchestrators. Understanding potential risks and how to protect your environment against them is essential.
Lack of visibility inside containers
Vulnerabilities can impact container images just like any other legacy code framework.
Container’s runtime have unknown behaviour
Container runtime is one of the most difficult parts of a container stack to secure because traditional security tools were not designed to monitor running containers. They can’t peer inside containers or establish good baselines for what a secure container environment looks like.
Registries
A container registry provides a convenient, centralized means of storing and distributing application images. Intrusions or vulnerabilities within the registry provide an easy opening for compromising running applications.
Lack of proper access control rules
Docker and Kubernetes use an explicitly whitelisted access model, also they have no protection for pod-to-pod communications which leaves room for attacks over the network and unwanted lateral movement.
How can this technology help you?
Provides container integrity
Ensures that the image inside a container has not changed from the approved one.
Containerized applications are typically easy to update quickly
What’s more, you can update particular containerized microservices without touching other services in the application. When you can update software quickly and easily, you can apply security patches more effectively.
Containers are a perfect building block for immutable infrastructure
In an immutable infrastructure architecture, components are totally replaced when they need to be updated, rather than modified while they are still running.
Advantages
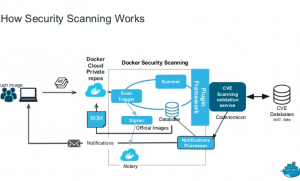
Image scanning and compliance
scanning of the images for vulnerabilities and compliance issues, identifying any embedded secrets or malware, and correlating risk to individual image layers ensures developers are building secure images.
Securing the registry
Continuously monitoring of the registries for any change in vulnerability status, locking down the server that hosts the registry and using secure access policies.
Container runtime protection
Establish behavioral baselines for container environments in a normal, secure state to detect and prevent anomalies or attacks. Runtime security allows security teams to focus on securing the application, rather than only relying on network-level security tools to keep them safe.
Orchestration
Security and infrastructure teams have proper access control measures to prevent risks from over-privileged accounts, attacks over the network and unwanted lateral movement.
Protection of the Host OS
hosts can be scanned for vulnerabilities and protected against improper access control (Docker commands, SSH commands, sudo commands, etc.) or file tampering.