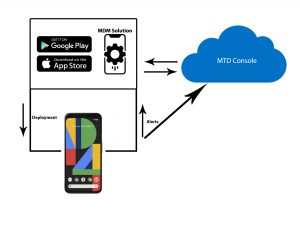
Mobile Threat Defence, MTD solutions protect mobile platforms by detecting threats to devices, operating systems, the networks they use and apps on the device. Each of these vectors is vulnerable to a variety of attack methods. However, some mobile threat defence solution providers cover all facets on the device in a single platform.
Given the growing popularity of smartphones as all-in-one computing devices for enterprise work and everyday personal use, it’s no wonder that mobile devices have become the most appealing attack surface for today’s cybercriminals and hackers to relentlessly attempt device, network and application attacks to gain an edge.
The number of reported cyber attacks targeting mobile devices has more than doubled every 6 months for the last three years. Given the growing popularity of smartphones as all-in-one computing devices for enterprise work and everyday personal use, it’s no wonder that mobile devices have become the most appealing attack surface for today’s cybercriminals and hackers to relentlessly attempt device, network and application attacks to gain an edge.
Challenges
Mobile devices face an increasingly complex web of security challenges. Not only must they be protected against conventional threats, like viruses, but it is important to protect against more sophisticated attacks: zero days attacks, man in the middle attacks, malware injection via some apps, even advanced network attacks.
Whether you are extending your existing antivirus and IT security measures to cover corporate-owned devices or implementing a bring-your-own-device (BYOD) policy, you need to look beyond the conventional IT security tools and policies for enterprise mobility management to address today’s advanced mobile threats.
How can this technology help you?
Mobile threat detection products focus on network – and behavior-based threats.
For instance, an MTD solution can detect man-in-the-middle attacks over Wi-Fi or identify suspicious device behavior. MTD is designed to detect malware and potentially harmful mobile applications as well as mobile phishing attacks. It can also remediate issues in a variety of ways, including the termination of a connection if it identifies a problem.
At a more technical level, a mobile threat detection solution can:
Monitor
Monitor a device’s configuration and system parameters and look for suspicious activity, such as the modification of system libraries.
Check
Check the integrity of Secure Sockets Layer (SSL) connections and website certificates and deactivate suspicious connections
Diagnose
Diagnose applications that may be “leaking” user data and detect potentially malicious apps through reputation scanning, code analysis, and malware filtering
MDM solutions generally come in one of two forms, either as an application that installs on the endpoint (smartphones in this case) and offer protection from that vantage point, or as SDKs that customers can include in their own applications, so that when their clients download and use their apps, they can still offer a high amount of protection on the unmanaged device.
Advantages
Confidence employing a BYOD policy
With MTD solutions, you can be more confident about allowing employees to use their own mobile devices for work purposes.
Faster response to threats
MTD will thwart attacks before they become serious problems.
Better visibility
With MTD, you’ll gain critical visibility into the risk level of the mobile workforce.
Regulatory compliance
Ensuring that sensitive data of the organization is safe regardless of where it sits.